Implemented firewall passthrough (STUN, TURN)
By reading through the following page, find out all the basic knowledge about those two protocols, Session Traversal Utilities for NAT (STUN) and Traversal Using Relay NAT (TURN) protocols, that can be used to implement firewall passthrough.
What you need to know about firewall passthrough
Increased penetration of broadband Internet is driving the adoption of Voice over Internet Protocol (VoIP) both for consumer and business markets, and VoIP is now on its way to becoming the main mode of multimedia communications in the coming years. But for something becoming so mainstream it is inevitable not to bump into some smaller difficulties on its way to popularity.
In case of VoIP technology this small bump is the issue of Network Address Translators, or shortly, NATs. NATs are common devices that translate private IP addresses to public IP addresses, this way, they 'hide' the private networks. It provides security but it also obstruct VoIP technology, because connections can only be initiated from the private network to the Internet, but not in reverse. Since VoIP's main essence is to establish connections both ways, this can mean a problem (Figure 1).
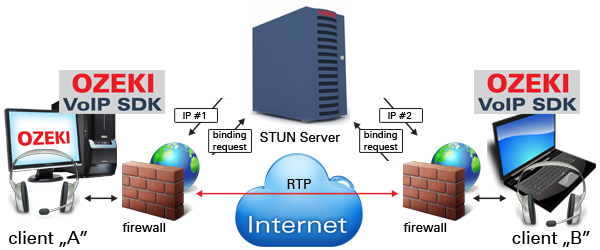
The same issue can also stand in case of an impenetrable firewall. Many firewalls only allow connections to be initiated from the private network. They commonly deny access to port numbers associated with VoIP. They can even inspect the packet contents to identify and reject VoIP traffic.
Now we have seen how NAT/firewalls present a challenge to VoIP call completion. But there are some clever solutions which have to be mentioned at this point. There are two protocols that can be helpful in this situation: STUN and TURN.
STUN is an acronym for Session Traversal Utilities for NAT. STUN is a lightweight client-server protocol requiring only simple query and response. The client side is implemented in the user's communications application, such as a Voice over Internet Protocol (VoIP) phone or instant messaging client. The base protocol operates essentially as follows. The client, often operating inside a private network, sends a binding request to a STUN server on the public Internet (Figure 1). The STUN server sends a success response that contains the IP address and port as observed from its perspective. The result is usually XOR mapped to avoid translation of packet contents.
Traversal Using Relay NAT protocol, in short term TURN is an extension for STUN protocol to facilitate NAT traversal when both endpoints are behind symmetric NAT. With TURN, media traffic for the session will have to go to a relay server. Since relaying is expensive, in terms of bandwidth that must be provided by the provider and additional delay for the media traffic, TURN is normally used as the last resort when endpoints cannot talk directly.
TURN and STUN implementation
Ozeki VoIP SIP SDK provides a great background support for all the technologies and functionalities that are mentioned above in this article. If you want to create a VoIP solution that has all this support, you only need to download, install and use Ozeki VoIP SIP SDK.
Examples on implementation:
- How to make calls through firewalls with NAT traversal
- How to use media handlers in softphone development
Summary
This article presented the basic concept of firewall passthrough and explained what are STUN and TURN protocols. You could also find some useful tutorial about their implementation. If you have read through this page carefully, you already have all the knowledge you need to start on your own solution.
If you have any question or need assistance, please contact us at info@voip-sip-sdk.com
Select a suitable Ozeki VoIP SIP SDK license for your project at: Pricing and licensing information
Related Pages
As you are now familiar with all the terms concerning this topic, now it is time to take a step further and explore what other extraordinary solution Ozeki VoIP SIP SDK can provide to you.
